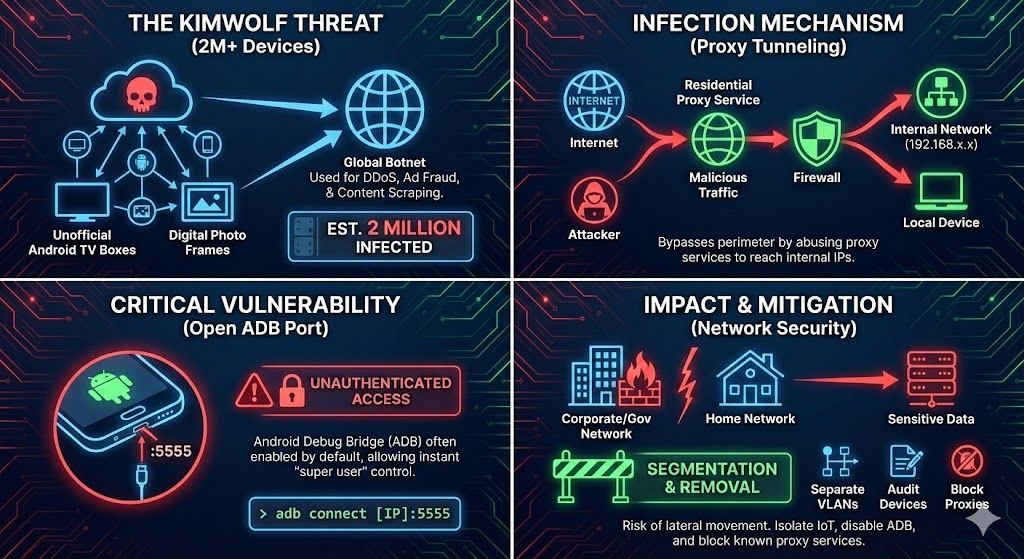
Kimwolf Botnet: The Silent Threat Inside Corporate and Government Networks
While the sheer size of the botnet (estimated at 1.8 to 2 million infected devices) is alarming, the primary concern is its ability to bypass traditional perimeter defenses.
Actions taken through the use of computer networks to disrupt, deny, degrade, or destroy information resident in computers and computer networks, or the computers and networks themselves.
While the sheer size of the botnet (estimated at 1.8 to 2 million infected devices) is alarming, the primary concern is its ability to bypass traditional perimeter defenses.
The company said it "promptly" initiated incident response and recovery measures after detecting "network anomalies." It also said it alerted law enforcement agencies of the matter.
The adversary behind the supply chain attack targeting 3CX deployed a second-stage implant specifically singling out a small number of cryptocurrency companies...
A .NET-based evasive crypter named DarkTortilla has been used by threat actors to distribute ..
The reward offer, first reported by WIRED, is also notable for the fact that it marks the first time the face of a Conti associate, known as "Target," has been unmasked. The four other associates have been referred to as "Tramp," "Dandis," "Professor," and "Reshaev."
The company revealed that the attackers could only harvest and steal non-sensitive data from a Box folder linked to a compromised employee's account.
A misconfigured Amazon S3 bucket resulted in 3TB of airport data (more than 1.5 million files) being publicly accessible, open, and without an authentication requirement for access, highlighting the dangers of unsecured cloud infrastructure within the travel sector.