Kimwolf Botnet: The Silent Threat Inside Corporate and Government Networks
While the sheer size of the botnet (estimated at 1.8 to 2 million infected devices) is alarming, the primary concern is its ability to bypass traditional perimeter defenses.
AI Trends & Cloud Security - CISSP & CCSP Resources
Click to Subscribe Free - CarlsCloud™ Members Only AccessWhile the sheer size of the botnet (estimated at 1.8 to 2 million infected devices) is alarming, the primary concern is its ability to bypass traditional perimeter defenses.
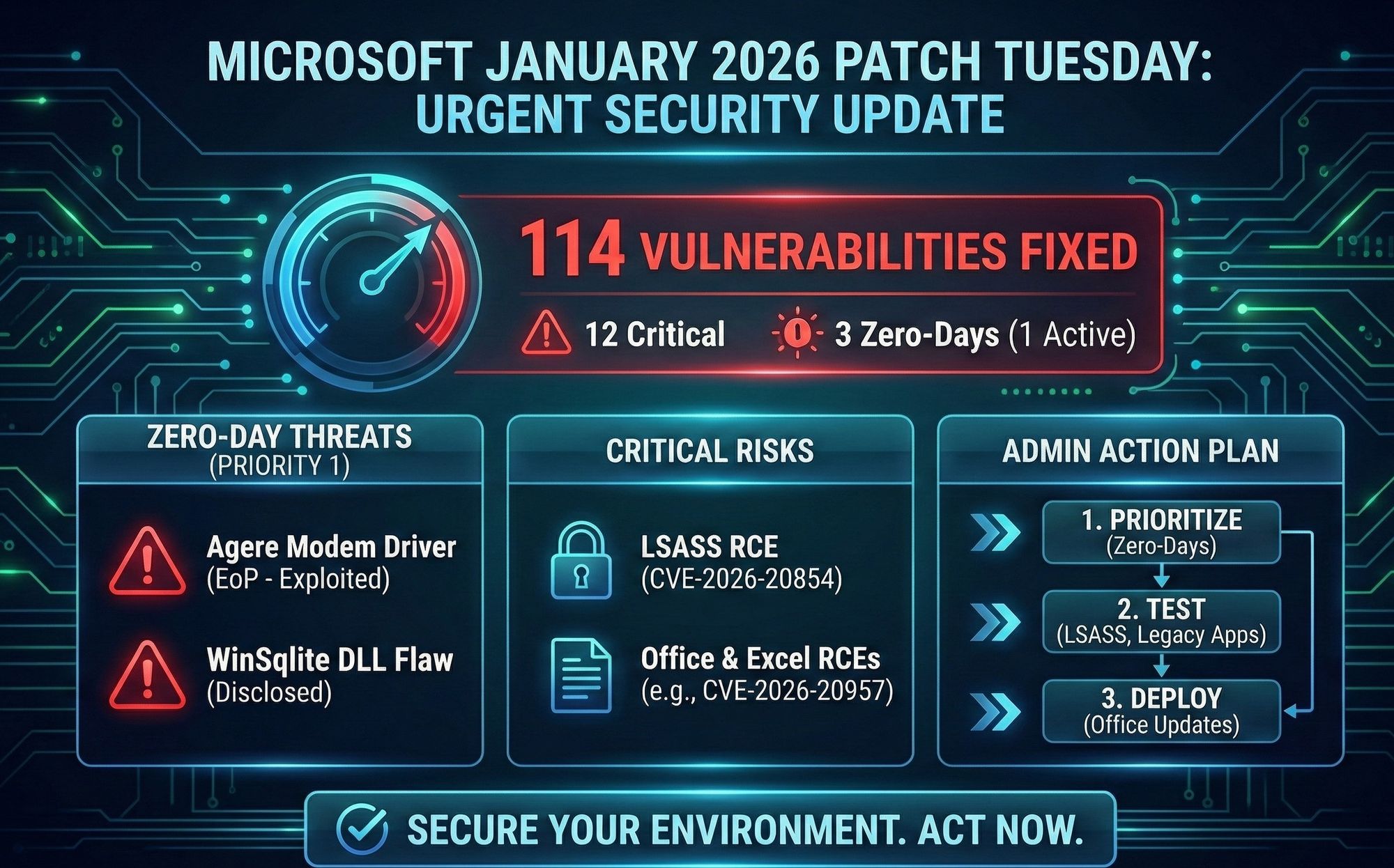
Microsoft kicks off 2026 with a massive security update, fixing 114 vulnerabilities and 3 zero-days. Here is what admins need to prioritize immediately.
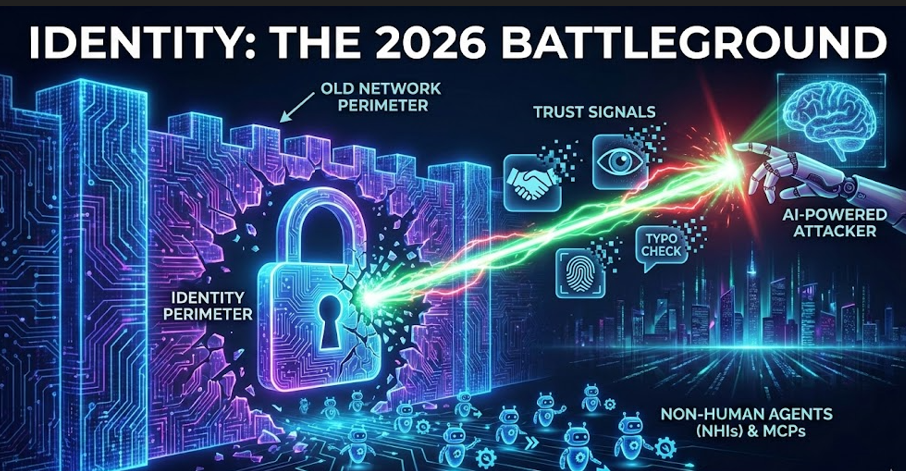
The consensus for 2026 is clear: Identity is the battlefield, but the rules of engagement have changed.
Affected Software & Versions The following React versions are vulnerable: 19.0 19.1.0 19.1.1 19.2.0
According to a Bloomberg report, the intrusion lasted for at least a year and has been attributed to UNC5221, a cyber espionage group with ties to China. The attackers reportedly used a malware family known as BRICKSTORM to maintain persistent access.
Hiring an external candidate can be a significant expense, with the average cost per hire in the U.S. at nearly $5,000, so the importance and value of retention during a period of economic pressure increases.
Understanding the concepts that underpin these answers is crucial for mastering the CISSP domains and effectively applying cybersecurity principles in real-world scenarios. Let's dive in!
This two-part blog series for questions #16-20 will present five CISSP mock exam questions followed by a questions #16-20 answers and explanations allowing you to assess your current understanding.
Took the CCSP exam and passed on the 1st attempt! Glad to get it done for sure and hoping to pay knowledge forward to help others out on their certification journey.