Kimwolf Botnet: The Silent Threat Inside Corporate and Government Networks
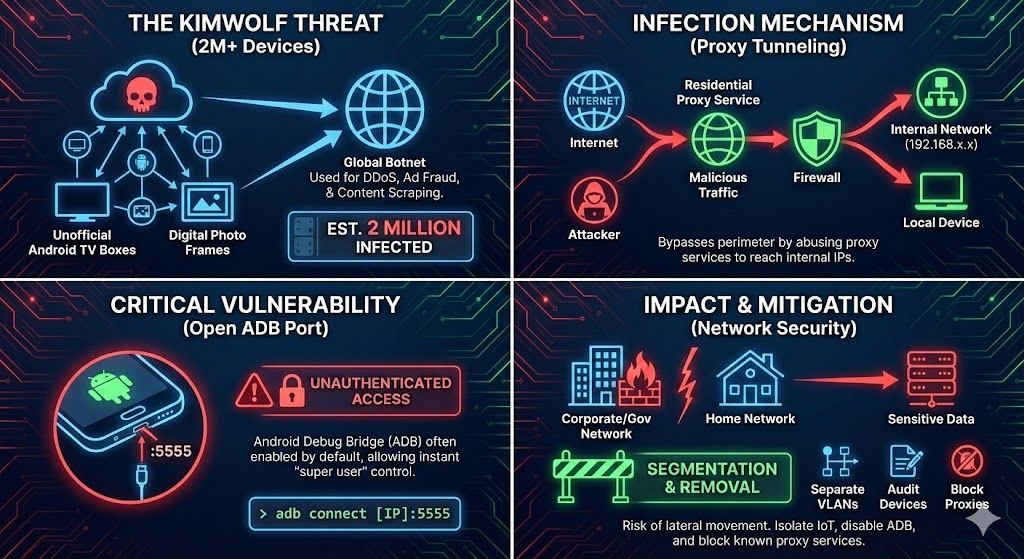
While the sheer size of the botnet (estimated at 1.8 to 2 million infected devices) is alarming, the primary concern is its ability to bypass traditional perimeter defenses.
Common Attack Vector Information and Related Articles
While the sheer size of the botnet (estimated at 1.8 to 2 million infected devices) is alarming, the primary concern is its ability to bypass traditional perimeter defenses.
Affected Software & Versions The following React versions are vulnerable: 19.0 19.1.0 19.1.1 19.2.0
A new audit reveals DeepSeek's iOS app transmits sensitive data unencrypted, has weak encryption, and collects excessive user data, raising serious security concerns.
The new python backdoor adds seven lines inside "/etc/rc.local.d/local.sh," one of the few ESXi files that survive between reboots and is executed at startup.
Per Twitter @Unit42_Intel a LockBit 3.0 variant using ESXi Locker version 1.2 continues targeting ESXi hash: 0f7c10dfa562adf15f1f6078ecaee788.
In part one, we covered attackers’ usage of malicious vSphere Installation Bundles (“VIBs”) to install multiple backdoors across ESXi hypervisors, focusing on the malware present within the VIB payloads. In
On Thursday September 29th, Mandiant published information on malware they discovered in the wild that leverages unsigned VIBs to install backdoors on a compromised ESXi host.
This malware ecosystem was initially detected during an intrusion investigation when Mandiant identified attacker commands sourced from the legitimate VMware Tools process, vmtoolsd.exe, on a Windows virtual machine hosted on a VMware ESXi hypervisor.