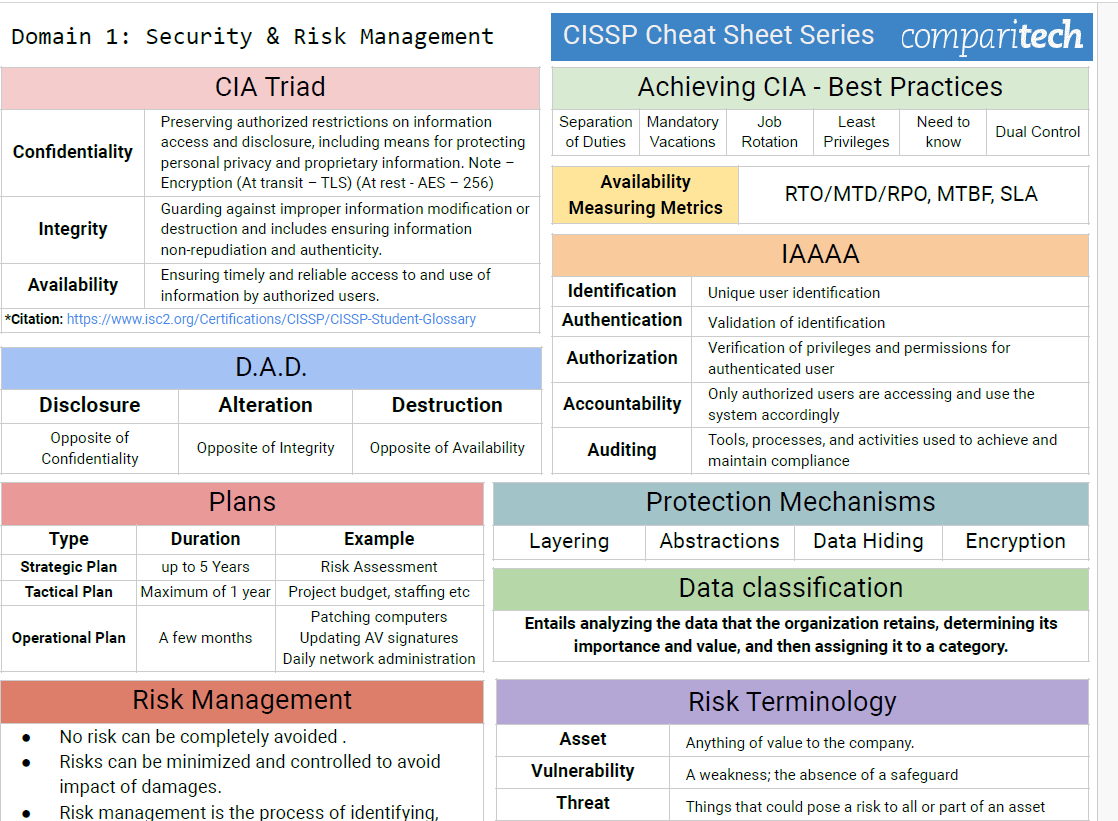
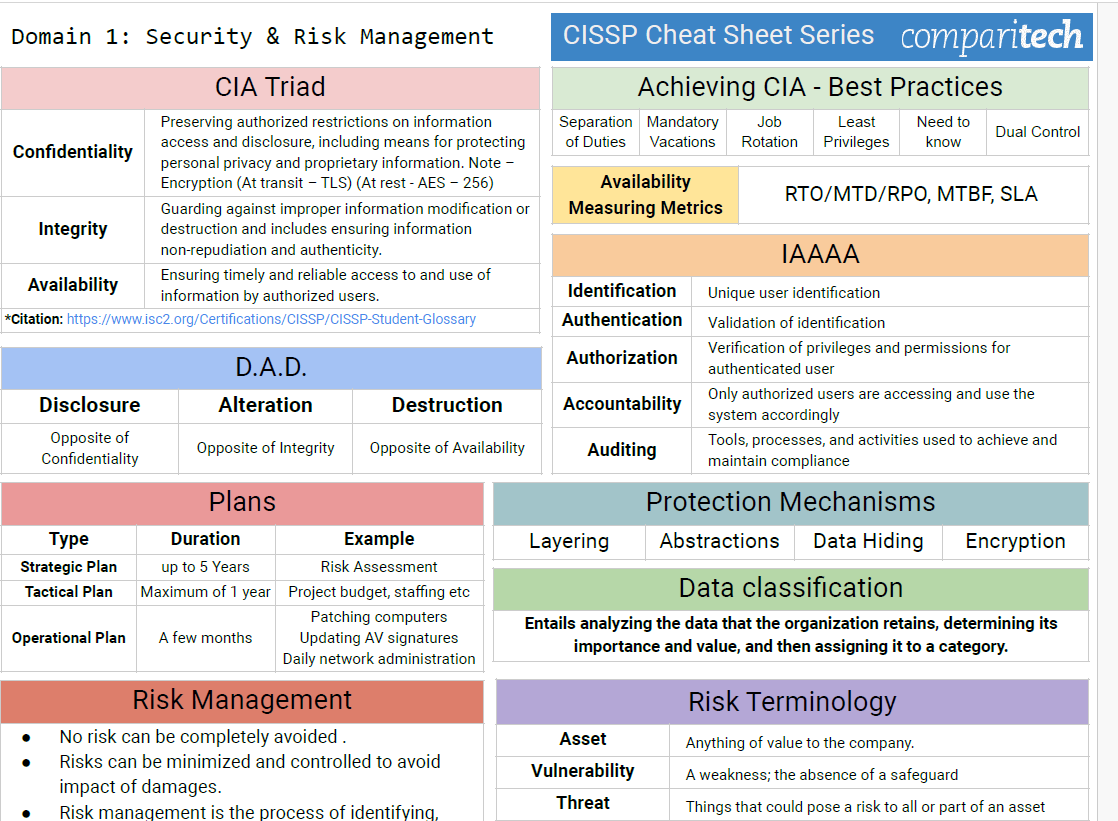
CISSP Domain 2: Asset Security centers around a core focus: safeguarding the value of your organization's assets. Whether it's intellectual property, sensitive data, critical infrastructure, or the resources that keep your business operational, Domain 2 provides the foundation for intelligent security decisions.
Mastering the Fundamentals
Let's break down the core concepts you'll need to understand for CISSP Domain 2 success:
- Data Classification: Organizing data based on sensitivity and criticality (e.g., confidential, internal use, public). This prioritizes your protection efforts.
- Data Ownership: Establishing clear roles and responsibilities for who manages and protects specific assets. Accountability is key!
- Privacy: Safeguarding personal information with adherence to regulations like GDPR and industry-specific laws. Privacy isn't optional; it's a duty.
- Retention Policies: Developing guidelines for how long data is stored, balanced against legal requirements and the organization's needs.
- Data Security Controls: Implementing safeguards like encryption, access control lists (ACLs), data loss prevention (DLP), and secure logging practices.
- Data Handling: Dictating secure methods for storing, processing, transmitting, and ultimately disposing of data throughout its lifecycle.
Why These Concepts Matter
In a world of continuous cyber threats, these aren't just textbook definitions. Domain 2 concepts form your proactive and actionable toolbox:
- Targeted Protection: A thorough understanding of data classification allows you to allocate resources most effectively, maximizing security.
- Clear Responsibility: Data ownership establishes clear lines of accountability and reduces finger-pointing when things go wrong.
- Regulatory Compliance: Knowing the ins and outs of privacy regulations and industry standards can prevent disastrous fines and loss of reputation.
- Protecting Business Value: Effective asset security practices underpin long-term business success. Data breaches hurt brand reputation, client trust, and a company's bottom line.
CISSP: A Journey of Understanding
Your mastery of Domain 2 provides a robust foundation for the subsequent CISSP domains. As you explore concepts like security architecture, communication security, and software development security, the principles you learn here will form the backbone of sound security decision-making.