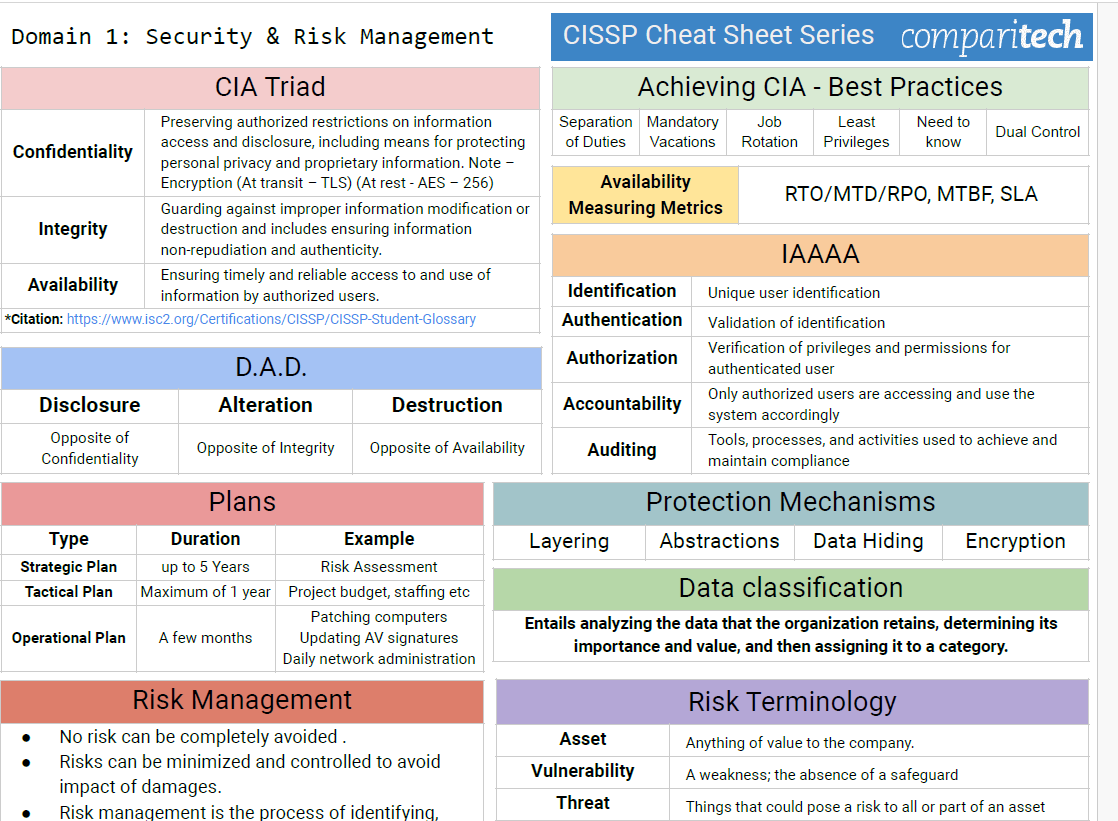
Encryption is your digital armor, but attackers wield the tools of cryptanalysis to find its chinks. Elevate your CISSP exam prep and cybersecurity expertise by outsmarting these attacks. Test your knowledge with our cryptanalysis technique quiz!
Scenario 1: A popular website suffers a data breach. User passwords, though encrypted, are quickly cracked. News reports blame a "weak hashing algorithm."
Which cryptanalytic concept is most relevant here?
- A. Brute Force Attack
- B. Chosen-Ciphertext Attack
- C. Rainbow Table Attack
- D. Social Engineering
Scenario 2: A new zero-day vulnerability is announced for a specific version of a widely used encryption library. Your organization must respond quickly.
From a CISSP perspective, what's your first priority?
- A. Decrypt all data using the vulnerable library ASAP
- B. Implement a side-channel attack
- C. Patch systems or replace the vulnerable library
- D. Analyze network traffic for signs of exploit attempts
Scenario 3: Threat intelligence indicates an attacker group is known to use a custom encryption algorithm when communicating with their malware.
Understanding the algorithm is key here. This likely involves which cryptanalysis type?
- A. Frequency Analysis
- B. Known-Plaintext Attack
- C. Reverse Engineering
- D. Quantum Cryptanalysis
Answer Key
Scenario 1: C (Rainbow Table Attack)
- Why: Rainbow tables are pre-computed hashes for common passwords. Weak hashing makes them devastatingly effective, regardless of password strength.
Scenario 2: C (Patch systems or replace the vulnerable library)
- Why: A CISSP prioritizes risk mitigation. Patching eliminates the known vulnerability fastest. Only then do you worry about advanced analysis.
Scenario 3: C (Reverse Engineering)
- Why: Custom malware encryption is a black box. Reverse engineering lets you dissect the algorithm for weaknesses to exploit or patch against.
Explanations: Why the Other Choices Are Less Ideal
Scenario 1
- Brute Force: Takes time, password strength matters more here.
- Chosen-Ciphertext: Active attack, not as relevant to already-breached data.
- Social Engineering: Tricks users, not relevant if crypto itself is flawed.
Scenario 2
- Decrypting Data: Unnecessary, risks exposing it more while vulnerable.
- Side-Channel Attack: Might be later, but not your immediate fix.
- Network Analysis: Good for detection, but patching stops the exploit at the source.
Scenario 3
- Frequency Analysis: Suits simple ciphers, not custom malware encryption.
- Known-Plaintext: Helps if you have that, but often you don't initially.
- Quantum Cryptanalysis: Emerging, but not your first tool against custom malware.
Key Takeaway: The CISSP exam tests your ability to prioritize actions based on risk and understanding the specific attack methods.
While you are here: Did you enjoy CarlsCloud™ CISSP Exam Resources related content today?
If so, buy me a coffee or just shoot me a note via LinkedIn to say thanks! It would certainly mean a lot to me!