Kimwolf Botnet: The Silent Threat Inside Corporate and Government Networks
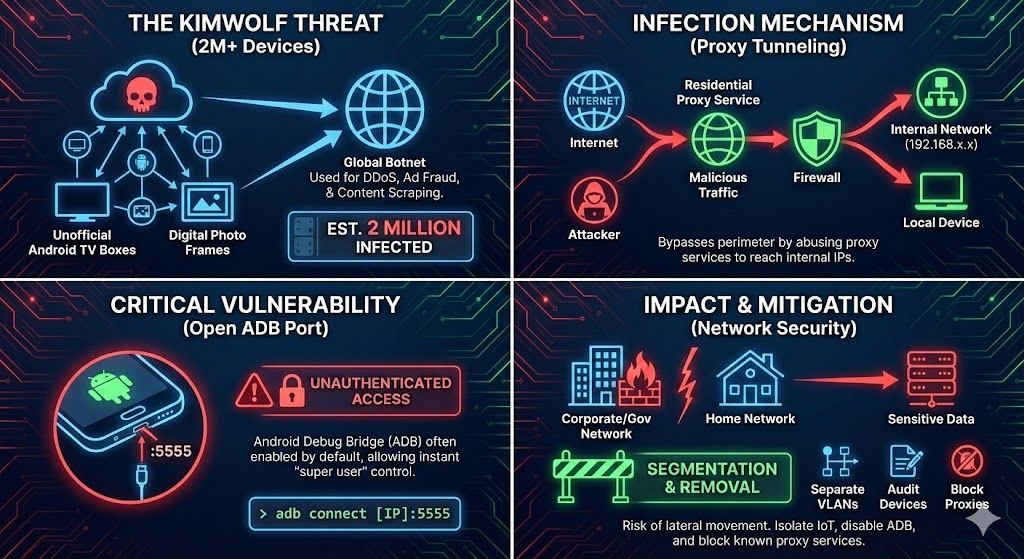
While the sheer size of the botnet (estimated at 1.8 to 2 million infected devices) is alarming, the primary concern is its ability to bypass traditional perimeter defenses.
Vulnerability is a weakness in an IT system that can be exploited by an attacker to deliver a successful attack. They can occur through flaws, features or user error, and attackers will look to exploit any of them, often combining one or more, to achieve their end goal.
While the sheer size of the botnet (estimated at 1.8 to 2 million infected devices) is alarming, the primary concern is its ability to bypass traditional perimeter defenses.
According to a Bloomberg report, the intrusion lasted for at least a year and has been attributed to UNC5221, a cyber espionage group with ties to China. The attackers reportedly used a malware family known as BRICKSTORM to maintain persistent access.
A new audit reveals DeepSeek's iOS app transmits sensitive data unencrypted, has weak encryption, and collects excessive user data, raising serious security concerns.
The vulnerability, tracked as CVE-2024-50050, has been assigned a CVSS score of 6.3 out of 10.0. Supply chain security firm Snyk, on the other hand, has assigned it a critical severity rating of 9.3.
Apple on Friday released security updates for iOS, iPadOS, macOS, and Safari web browser to address a pair of zero-day flaws that are being exploited in the wild.
The new python backdoor adds seven lines inside "/etc/rc.local.d/local.sh," one of the few ESXi files that survive between reboots and is executed at startup.
Per Twitter @Unit42_Intel a LockBit 3.0 variant using ESXi Locker version 1.2 continues targeting ESXi hash: 0f7c10dfa562adf15f1f6078ecaee788.
In part one, we covered attackers’ usage of malicious vSphere Installation Bundles (“VIBs”) to install multiple backdoors across ESXi hypervisors, focusing on the malware present within the VIB payloads. In