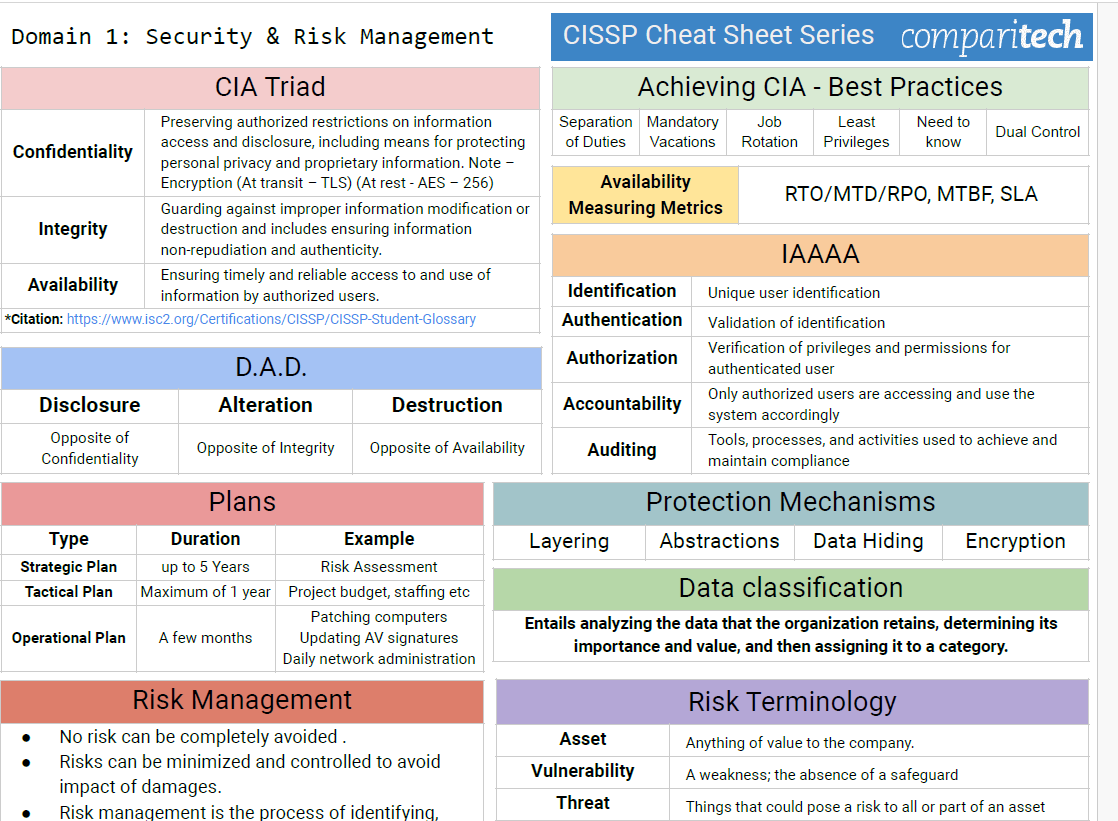
The CISSP exam loves to test your understanding of how security concepts apply across the entire network stack.
Let's tackle some tricky scenarios focused on the OSI Model – can you pinpoint the core issue and the OSI layer at the heart of the problem?
CarlsCloud™ Scenario #1: The Case of the Elusive Connection
The company new web server is installed and online. However, users on the internal network cannot access it. Ping tests are successful, but web browsers time out.
Which OSI layer is the MOST likely culprit?
- Layer 1 (Physical)
- Layer 3 (Network)
- Layer 4 (Transport)
- Layer 7 (Application)
CarlsCloud™ Scenario #2: Wi-Fi Woes
Users complain of slow wireless speeds and spotty connections. Nearby corporate wireless networks are operating on overlapping channels.
This problem primarily stems from which OSI layer?
- Layer 1 (Physical)
- Layer 2 (Data Link)
- Layer 3 (Network)
- Layer 5 (Session)
CarlsCloud™ Scenario #3: A Firmware Fiasco
A critical vulnerability is found in the firmware of your core network routers. The patch instructions involve complex updates.
Updating router firmware can potentially impact multiple OSI layers. Which of the following is LEAST likely to be directly involved?
- Layer 2 (Data Link)
- Layer 3 (Network)
- Layer 5 (Session)
- Layer 7 (Application)
CarlsCloud™ Scenario #4: Phishing Frenzy
A phishing campaign delivers emails with malicious links disguised as invoices. Users who click are redirected to fake login pages that steal credentials.
While this attack involves several layers, which OSI layer is the initial entry point?
- Layer 4 (Transport)
- Layer 6 (Presentation)
- Layer 7 (Application)
- Layer 8 (User) 😉?
Beyond the Answers: Why This Matters for the CISSP
- Troubleshooting: Real-world problems rarely fit neatly into one layer. Knowing the OSI model helps isolate the root cause.
- Security Controls: Defense-in-depth means implementing security at multiple layers A CISSP must understand their interplay.
- Exam Questions: The CISSP loves throwing in those "choose the MOST likely" scenarios. The OSI model is your guide to narrowing it down.
CarlsCloud™ OSI Model Mayhem: Answers and Explanations
Ready to dissect those tricky OSI scenarios from our last quiz? Let's break down why the chosen answers are most likely and how the OSI model helps us think through these multi-layered problems.
CarlsCloud™ Answer Key & Explanations
Scenario #1
Answer: Layer 4 (Transport)
- The Breakdown: Successful pings tell us the basic network connection (up to Layer 3) is fine. Web browsers use higher-level protocols like HTTP (Layer 7), which rely on the underlying TCP (Layer 4) to establish connections. Likely culprits here are firewall rules, port misconfigurations, or web server issues.
Scenario #2
Answer: Layer 1 (Physical)
- The Breakdown: Wireless channels operate within specific radio frequencies, part of the physical layer. Overlap means signals are literally interfering with each other, causing transmission errors and slow speeds. Solutions involve changing wireless channels or physical reconfiguration of access points.
Scenario #3
Answer: Layer 5 (Session)
- The Breakdown: While tricky (notice LEAST is used as the qualifier in the true answer being found), and this one's about process. Firmware updates can contain changes to everything from routing protocols (Layer 3) to how MAC addresses are handled (Layer 2). Sessions, however, are higher-level logical connections that wouldn't be directly manipulated with firmware changes.
Scenario #4
Answer: Layer 7 (Application)
- The Breakdown: Phishing begins with exploiting the email application itself or user behavior, both firmly in Layer 7 territory. The malicious link then misuses HTTP (also Layer 7), but the attack's success hinges on the initial compromise of the email application/user interaction.
The CISSP Mindset Takeaway
The OSI model isn't about memorization – it's about a framework for understanding "WHERE" problems can occur.
Here's the deeper lesson:
- Interactions Matter: Security vulnerabilities often cascade through layers. A phishing email's success (Layer 7) can lead to network compromise (Layer 3 and below).
- Troubleshooting Mindset: Start by isolating – do we even have basic connectivity? Then move up the stack to pinpoint the problem.
- Beyond the Model: The real world isn't always as clean as the OSI model. But it remains a powerful tool for narrowing down complex issues.
For a deeper dive into the OSI model see below:
While you are here: Did you enjoy CarlsCloud™ CISSP related content today?
If so, buy me a coffee or just shoot me a note via LinkedIn to say thanks! It would mean a lot to me!