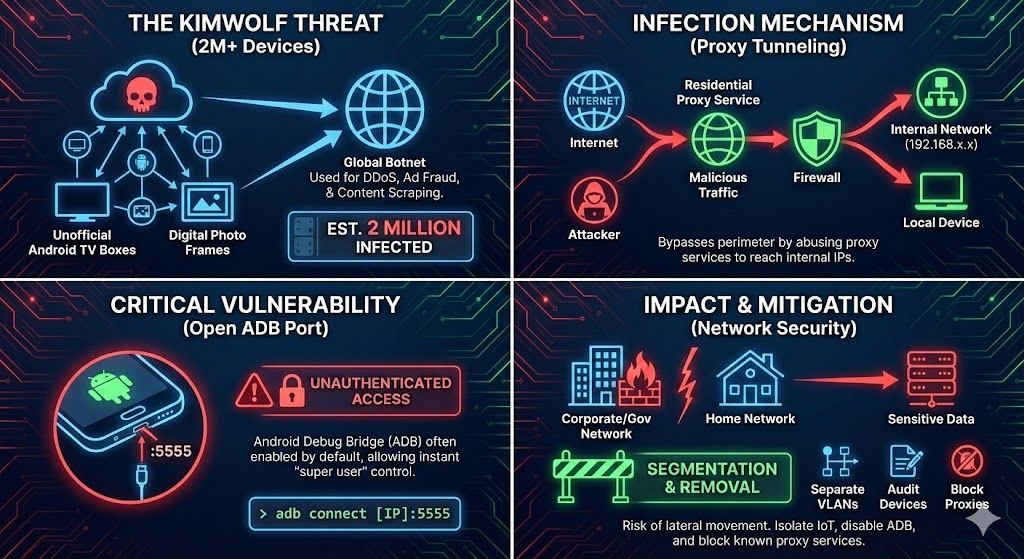
A new ransomware family dubbed Luna can be used to encrypt devices running several operating systems, including Windows, Linux, and ESXi systems.
Discovered by Kaspersky security researchers via a dark web ransomware forum ad spotted by the company's Darknet Threat Intelligence active monitoring system, Luna ransomware appears to be specifically tailored to be used only by Russian-speaking threat actors.
"The advertisement states that Luna only works with Russian-speaking affiliates. Also, the ransom note hardcoded inside the binary contains spelling mistakes. For example, it says 'a little team' instead of 'a small team'," Kaspersky said.
"Because of this, we assume with medium confidence that the actors behind Luna are speakers of Russian."
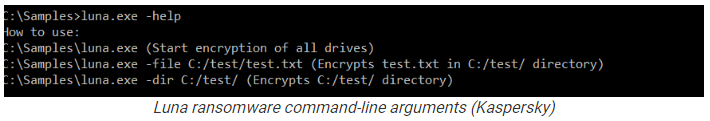
Luna (Russian for moon) is very simple ransomware still under development and with limited capabilities based on the available command line options.
However, it uses a not-so-common encryption scheme, combining fast and secure X25519 elliptic curve Diffie-Hellman key exchange using Curve25519 with the Advanced Encryption Standard (AES) symmetric encryption algorithm.
Rust-based cross-platform ransomware
The group behind this new ransomware developed this new strain in Rust and took advantage of its platform-agnostic nature to port it to multiple platforms with very few changes to the source code.
Using a cross-platform language also enables Luna ransomware to evade automated static code analysis attempts.
"Both the Linux and ESXi samples are compiled using the same source code with some minor changes from the Windows version. The rest of the code has no significant changes from the Windows version," the researchers added.
Luna further confirms the latest trend adopted by cybercrime gangs developing cross-platform ransomware that use languages like Rust and Golang to create malware capable of targeting multiple operating systems with little to no changes.
Kaspersky says there is very little data on what victims have been encrypted using Luna ransomware, if any, given that the group has just been discovered and its activity is still being monitored.
Other new ransomware families BleepingComputer reported this month include Lilith, C/C++ console-based ransomware targeting 64-bit Windows devices, and 0mega, a new ransomware operation targeting enterprises since May and demanding millions of dollars in ransoms.
Both are known for stealing data from victims' networks before encrypting their systems in support of their double-extortion attacks.