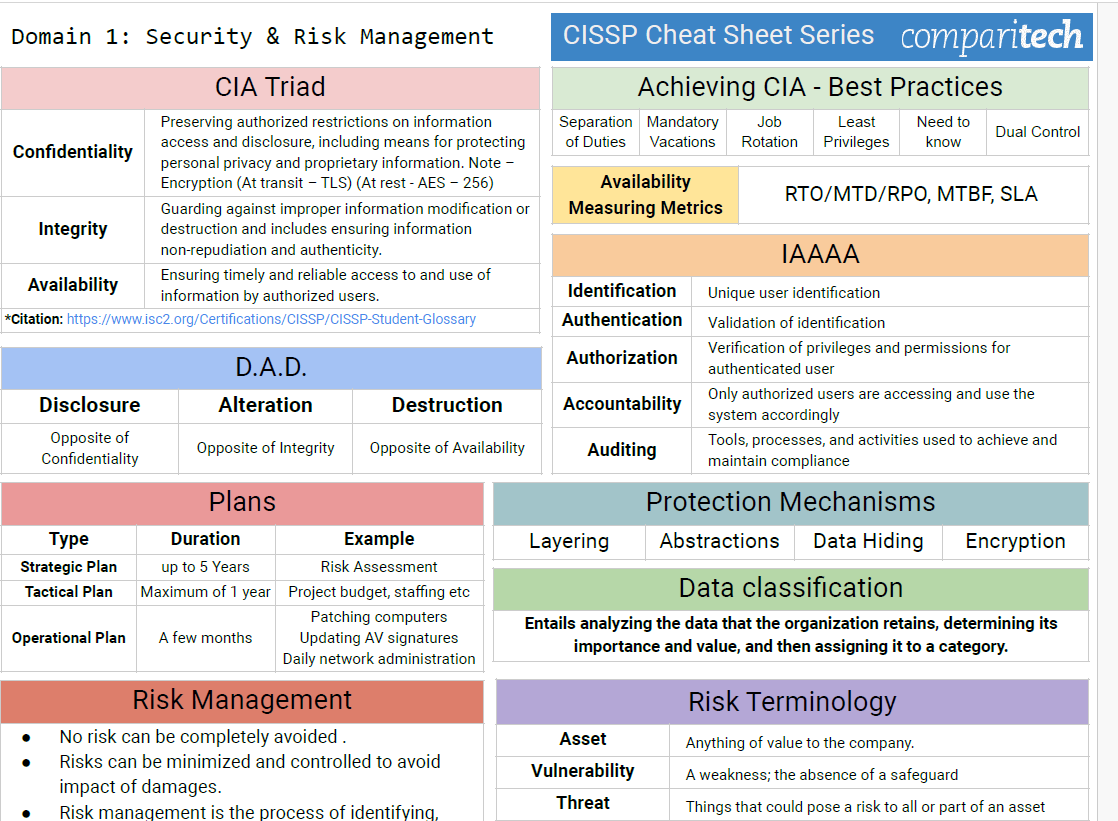
Think you know MFA? Domain 5 of the CISSP goes beyond simple implementation and into the nuances of when and how to use it effectively.
Sharpen those critical thinking skills with a tougher MFA quiz!
A CarlsCloud™ - Advanced MFA Pop Quiz
Scenario 1: Your organization handles highly sensitive health data. Regulatory requirements mandate strict access controls. MFA is already used, but additional measures are needed.
Which option offers the MOST robust security in this scenario?
- A. SMS-based one-time codes for all logins
- B. Hardware tokens generating time-based codes
- C. MFA only for accounts accessing patient records
- D. Context-aware MFA: location, device, time of day all factor in
Scenario 2: MFA rollout is planned for a legacy on-premises system with limited integration capabilities. Budget for upgrades is minimal.
Given these constraints, what's the MOST feasible MFA approach?
- A. Fingerprint readers attached to workstations
- B. Software tokens that users install on their personal phones.
- C. Push notifications to a dedicated company-issued mobile app
- D. No MFA is possible for this type of system
Scenario 3: News of zero-day vulnerabilities in a popular MFA vendor's software emerge. A patch isn't immediately available.
What's the best course of action from a CISSP perspective?
- A. Immediately disable MFA across all systems until patched
- B. Enforce complex password changes to compensate
- C. Issue hardware tokens as temporary replacements
- D. Assess risk, implement compensating controls where possible
The CISSP Mindset and Headspace for exam questions
- No Silver Bullet: MFA is powerful, but not foolproof. Exam questions test your understanding of its limitations.
- Risk-Based Approach: The "best" MFA depends on data sensitivity, threats, and the organization's constraints.
- Contingency Planning: How do you mitigate the failure of a security control?
Here's the answer key for our advanced MFA quiz, along with explanations for why those choices are the most likely from a CISSP mindset perspective.
Answer Key
Scenario 1 = Answer: D (Context-aware MFA)
- Why: Highly sensitive data and regulations demand maximum protection. Context awareness adds layers (location, trusted devices, unusual behavior) without overly hindering usability.
Scenario 2 = Answer: B (Software tokens on personal phones)
- Why: Legacy systems and tight budgets limit options. While not perfect, software tokens are implementable without extra hardware or extensive system changes.
Scenario 3 = Answer: D (Assess risk, implement compensating controls)
- Why: A CISSP balances security and operations. Disabling MFA entirely is too drastic. Risk assessment guides where tighter password policies, increased monitoring, or temporary restrictions may mitigate risk until a patch is available.
Explanations: Why the Other Answers Are Less Ideal
Scenario 1
- SMS Codes: Known to be vulnerable to interception and SIM-swapping attacks. Not enough for high-risk data.
- Hardware Tokens: While strong, the cost and logistics are higher than other options.
- MFA Only for Some Accounts: Leaves a major attack vector for less-protected accounts.
Scenario 2
- Fingerprint Readers: Requires specific hardware, can't work with legacy systems.
- Dedicated App: Development cost is likely prohibitive given the budget constraints.
- No MFA: A CISSP would never fully remove a security control on a legacy system.
Scenario 3
- Disable MFA: Unacceptable risk exposure, especially as MFA is a defense against password compromise.
- Complex Passwords: Good practice always, but insufficient on their own to counter a zero-day in MFA itself.
- Hardware Tokens: A good long-term fix, but a logistical nightmare to deploy quickly as a stopgap.
While you are here: Did you enjoy CarlsCloud™ CISSP related content today?
If so, buy me a coffee or just shoot me a note via LinkedIn to say thanks! It really would mean a lot to me!