
Articles


CarlsCloud™ Overview of NIST Cybersecurity Framework 2.0
Direct PDF link for CSF 2.0: https://doi.org/10.6028/NIST.CSWP.29
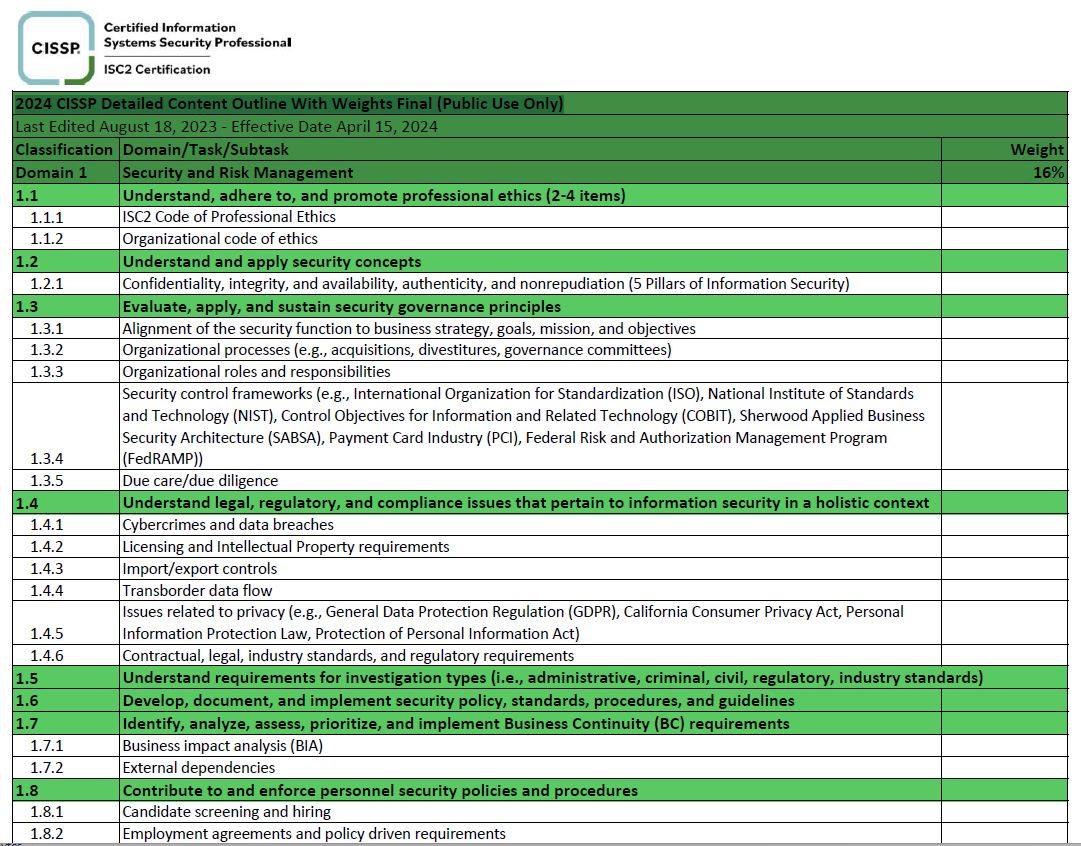
CarlsCloud™ CISSP Domain 5: IAM Scenarios: Pop Quiz Can You Crack the Code?
Name the IAM Concept" Quiz Scenario 1: During a security audit, it's discovered that several administrative accounts have far more permissions than necessary for their job roles.
CarlsCloud™ CISSP Domain 5: Identity & Access Management MFA: Beyond the Basics – A CISSP-Level Pop Quiz
Think you know MFA? Domain 5 of the CISSP goes beyond simple implementation and into the nuances of when and how to use it effectively.
CarlsCloud™ OSI Model Mayhem: A CISSP Exam Pop Quiz
CarlsCloud™ Let's tackle some tricky scenarios focused on the OSI Model – can you pinpoint the core issue and the OSI layer at the heart of the problem?

CarlsCloud™ Master the Pomodoro® Technique for CISSP Exam Success
Strategic Time Management: Applying Pomodoro® Technique
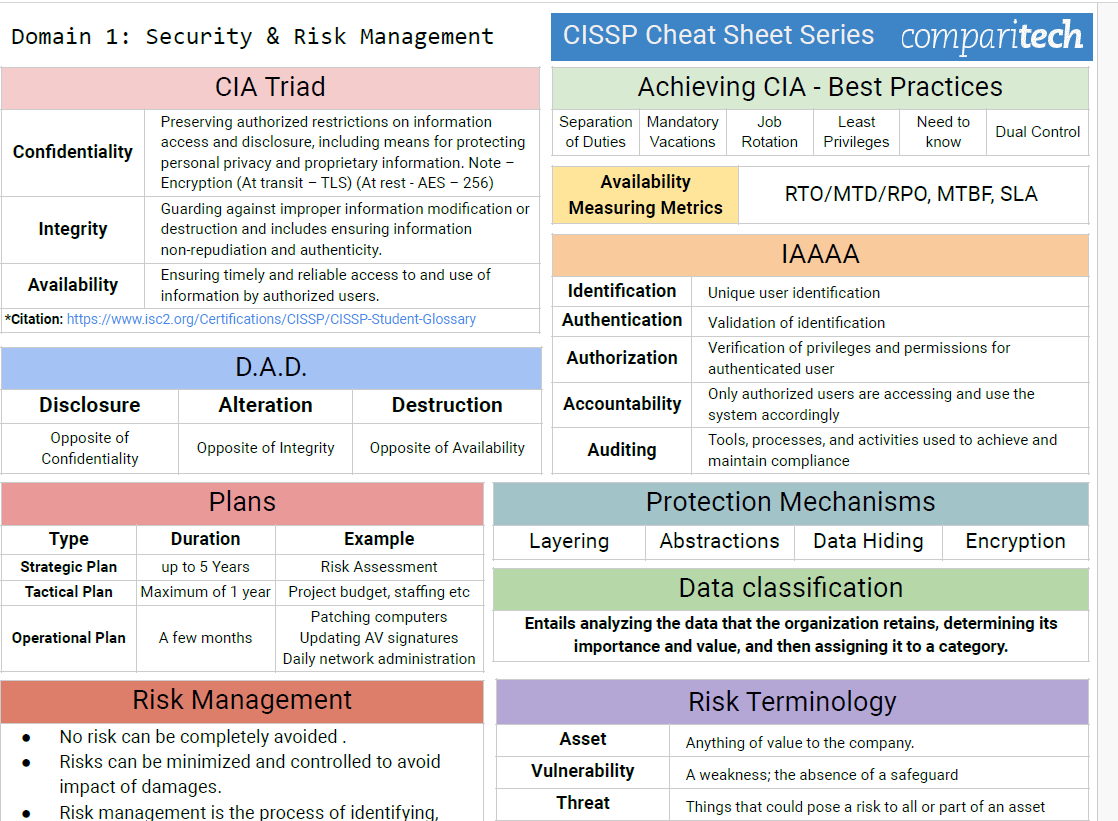
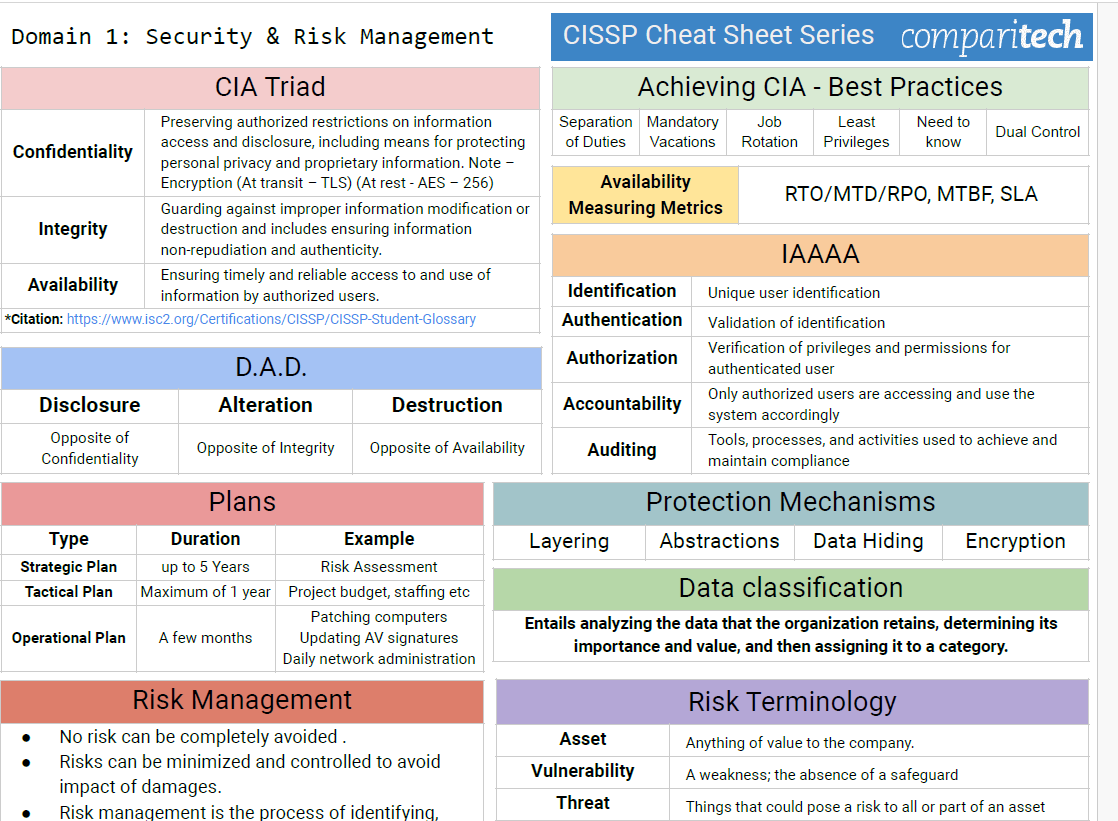
CarlsCloud™ Unveiling CISSP Domain 2: Essential Concepts for Asset Security
Mastering the Fundamentals Let's break down the core concepts you'll need to understand for CISSP Domain 2 success:

CarlsCloud™ The NIST Know-How Challenge: Test Your CISSP Publication Smarts
Get ready to flex your CISSP knowledge! The National Institute of Standards and Technology (NIST) produces tons of guidelines and frameworks directly relevant to many CISSP domains.