Welcome to the first Patch Tuesday of 2026.
If you were hoping for a quiet start to the new year, Microsoft had other plans.
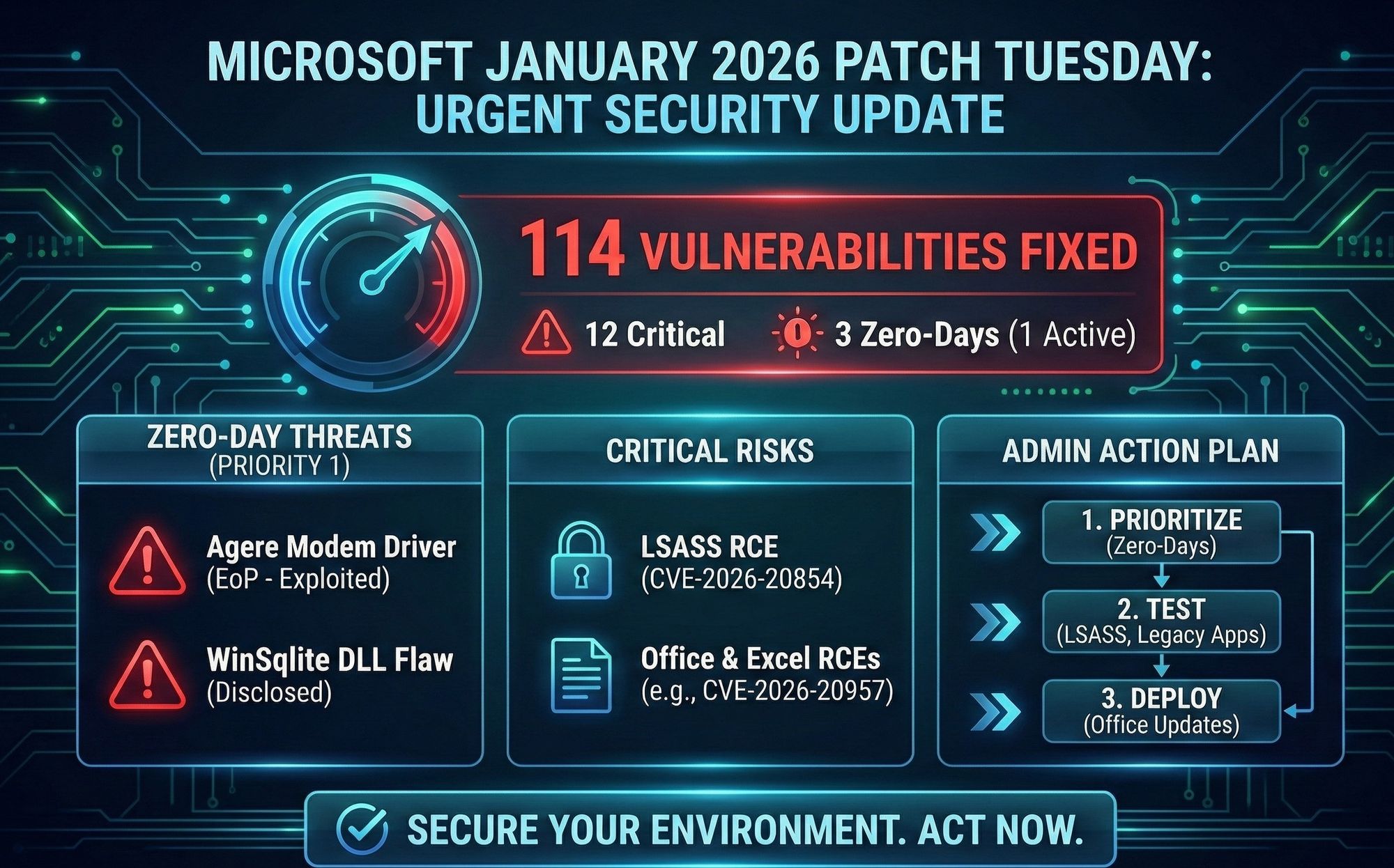
This month, Redmond has released a substantial security update addressing 114 vulnerabilities across its ecosystem. The release is heavy on critical risks, patching 12 Critical flaws and, most importantly, 3 zero-day vulnerabilities—one of which is already being actively exploited in the wild.
For system administrators and security teams, the holiday break is officially over. Here is everything you need to know to secure your environment this month.
The January 2026 Breakdown
The volume of patches this month is significantly higher than recent averages, signaling a busy year ahead for patch management.
- Total Vulnerabilities Fixed: 114
- Critical Vulnerabilities: 12
- Zero-Days: 3 (Includes actively exploited flaws)
- Remote Code Execution (RCE): 22
The updates cover a wide range of products, including Windows, Office, SharePoint, .NET, and SQL Server. However, the most urgent attention should be directed toward the Windows Kernel, LSASS, and Office components.
Priority 1: The Zero-Day Threats
This month's most pressing issues are the zero-day vulnerabilities. These are flaws that were either publicly disclosed or exploited before a patch was available.
Actively Exploited Agere Modem Driver
Microsoft has patched an Elevation of Privilege (EoP) vulnerability in the built-in Agere modem drivers. While modem drivers might feel like legacy tech, they remain a viable attack vector in legacy codebases.
- Risk: Attackers can abuse this to gain higher privileges on a compromised machine.
- Action: Verify the installation of KB5073724 immediately.
2. WinSqlite DLL Security Flaw
A second zero-day involves the third-party WinSqlite DLL, a core component used by Windows for database operations. This flaw has been publicly disclosed, increasing the risk that threat actors will reverse-engineer the vulnerability to create exploits.
Critical Remote Code Execution (RCE) Risks
Beyond the zero-days, massive RCE risks lurk in this update. If left unpatched, these could allow attackers to run arbitrary code on your network.
The Local Security Authority Subsystem Service (LSASS) is a favorite target for attackers (often used to dump credentials).
- The Flaw: A use-after-free error that allows remote code execution over the network.
- Severity: Critical. This affects the core authentication mechanism of Windows.
Microsoft Office & Excel RCEsThe Office suite received multiple critical patches this month, specifically targeting:
- Excel: Multiple pointer issues and integer underflows (e.g., CVE-2026-20957).
- Word: Out-of-bounds read vulnerabilities (CVE-2026-20944).
Note: These Office exploits often rely on the Preview Pane. Disabling the Preview Pane in Outlook and Explorer can offer temporary mitigation until patches are deployed.
Important Admin Changes for 2026
Windows Server 2025 KB Identifiers
Starting with this update, Microsoft is changing how it labels updates for its newest server OS. Windows Server 2025 will now have its own unique KB identifiers, separate from Windows 11 versions.
- Why it matters: If you rely on automated scripts or manual catalog searches, ensure you are looking for the Server-specific KBs, or your deployments may fail.
Secure Boot Certificate Renewal
Microsoft is rolling out updates to address expiring Secure Boot certificates. This is a phased rollout to prevent boot failures.
- The Plan: Devices will receive new certificates only after they demonstrate "sufficient successful update signals."
- Pro Tip: Do not force these updates manually unless necessary; let the automated servicing stack handle the prerequisite checks to avoid bricking bootloaders.
January 2026 sets a serious tone for the year. With over 100 fixes and active exploitation in the wild, "wait and see" is not a viable strategy this month.
Your Action Plan:
- Prioritize: Patch workstations and servers for the Agere Modem and WinSqlite zero-days immediately.
- Test: Validate the LSASS patches in a staging environment, as authentication fixes can sometimes cause friction with legacy apps.
- Deploy: Roll out Office updates to protect users from malicious file attachments.
Official Microsoft Documentation
- Security Update Guide (Searchable Database):
https://msrc.microsoft.com/update-guide/ - KB5073724 (Windows 10 Extended Security Update
https://support.microsoft.com/help/5073724 - KB5074109 (Windows 11 Cumulative Update):
https://support.microsoft.com/help/5074109 - Windows Message Center (Release Health):
https://learn.microsoft.com/en-us/windows/release-health/windows-message-center
Stay vigilant and happy patching!