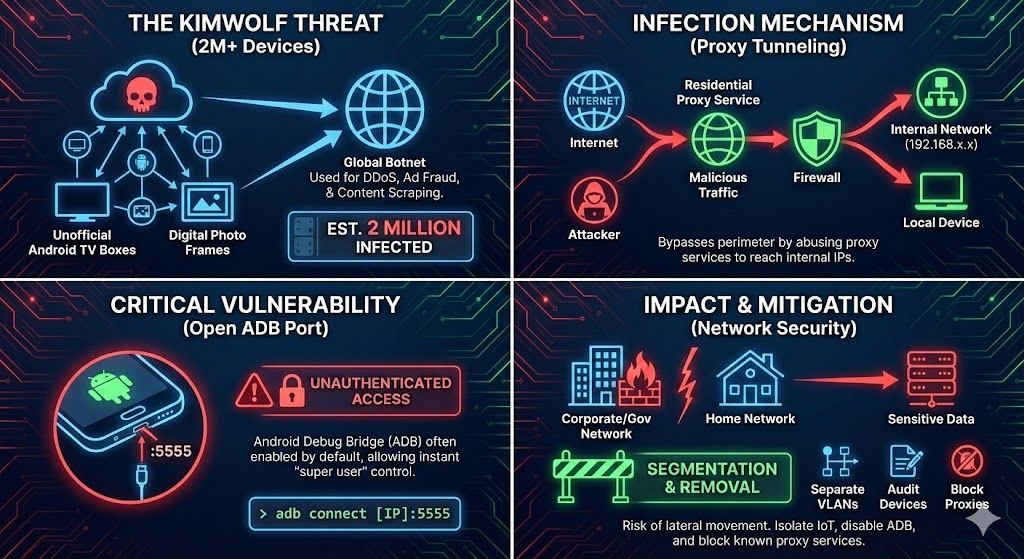
A new and aggressive botnet known as Kimwolf has rapidly infected over two million devices globally, exposing a critical vulnerability in how internal networks—from home offices to corporate and government environments—are secured.
The Threat Landscape
Security researchers from Synthient and the Chinese firm XLab have tracked the explosive growth of Kimwolf, which primarily targets unofficial Android TV streaming boxes and internet-connected digital photo frames. These low-cost devices, often sold on major e-commerce platforms like Amazon and Walmart, frequently ship with no built-in security or authentication.
While the sheer size of the botnet (estimated at 1.8 to 2 million infected devices) is alarming, the primary concern is its ability to bypass traditional perimeter defenses.
Infoblox reviewed its customer traffic and found 25% made queries to Kimwolf related domain names since Oct. 1st , 2025.
“To be clear, this suggests that nearly 25% of customers had at least one device that was an endpoint in a residential proxy service targeted by Kimwolf operators,” Infoblox explained. “Such a device, maybe a phone or a laptop, was essentially co-opted by the threat actor to probe the local network for vulnerable devices. A query means a scan was made, not that new devices were compromised. Lateral movement would fail if there were no vulnerable devices to be found or if the DNS resolution was blocked.”
Mechanism of Attack: Tunneling Through Proxies
Kimwolf utilizes a sophisticated method to breach local networks:
Residential Proxy Abuse: The botnet leverages "residential proxy" services—networks that allow users to route traffic through legitimate residential IP addresses to anonymize their location.
RFC-1918 Bypass: Researchers discovered that Kimwolf operators could manipulate Domain Name System (DNS) settings to target internal IP ranges (such as192.168.x.xor10.x.x.x). This allows attackers to "tunnel" back through a proxy user's connection and communicate directly with other devices on that user's local network.
ADB Exploitation: Many infected Android devices ship with the Android Debug Bridge (ADB) enabled by default. This diagnostic tool, intended for manufacturing, leaves the device listening for unauthenticated commands. Attackers can simply connect to port 5555 and gain "super user" administrative access instantly.
Government and Corporate Implications
The threat extends beyond consumer living rooms. The ability to tunnel into local networks makes Kimwolf a potent tool for reconnaissance and lateral movement within enterprise and government environments.
Recent reports indicate that federal agencies, including the Drug Enforcement Administration (DEA), are investigating incidents where hackers may have used similar proxy-tunneling techniques to gain unauthorized access to agency portals and law enforcement databases. This suggests that "smart" devices connected to guest or corporate networks could serve as trojan horses, bypassing firewalls to expose sensitive internal infrastructure.
Key Findings and Attribution
- Origin: The botnet is believed to be an evolution of the earlier Aisuru botnet, with code analysis revealing shared infrastructure and specific "easter eggs" referencing security researchers.
- Infrastructure: The botnet relies heavily on the IPIDEA proxy network. Investigations revealed a near-perfect overlap between new Kimwolf infections and IP addresses sold by IPIDEA.
- Monetization: Infected devices are monetized in multiple ways, including participation in massive Distributed Denial of Service (DDoS) attacks, ad fraud, and mass content scraping.
Mitigation Recommendations
Security experts advise the following immediate steps:
Device Audit: Identify and remove unsanctioned "grey market" Android TV boxes or cheap IoT devices from the network.
Network Segmentation: Strictly isolate IoT devices on a separate VLAN (Virtual Local Area Network) that cannot communicate with critical computers, servers, or sensitive data repositories.
Disable ADB: If such devices must be used, ensure developer options and ADB are disabled.
Proxy Blocking: Enterprise firewalls should block connections to known residential proxy services and restrict DNS resolution for internal IP ranges from external sources.
Additional Resources:
XLab Technical Report: "Kimwolf Exposed
This is the primary technical source mentioned in the rewritten article. It details the botnet's command-and-control infrastructure, the specific "easter eggs" found in the code, and the methodology used to estimate the 1.8+ million infection count.
Quokka Security Advisory: Uhale Digital Picture FramesLink
This report focuses specifically on the "digital photo frame" infection vector. It explains the vulnerabilities in the Uhale app and Android-based frames that allow Kimwolf to gain root access and persist on the network.
KrebsOnSecurity: Part II – Who Benefited from the Aisuru and Kimwolf Botnets?
The follow-up investigation teased in the original article. This piece dives into the financial ecosystem behind the botnet, linking the operators to specific residential proxy providers like IPIDEA and analyzing the "follow the money" trail.