Ready to dive into those subtle-but-significant network security flaws? Last time we presented a configuration scenario designed to push your Domain 4 expertise.
Let's break down the issues based on the following and how to address them.
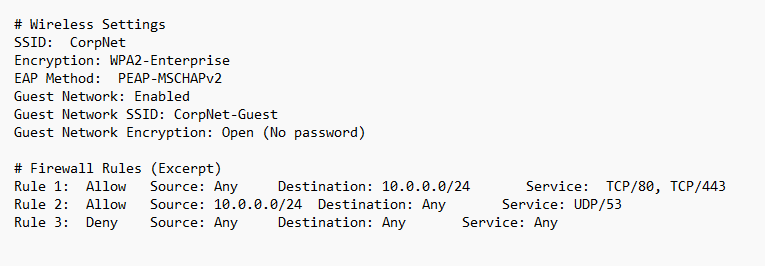
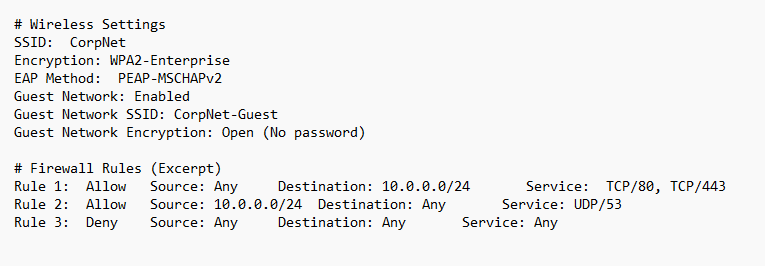
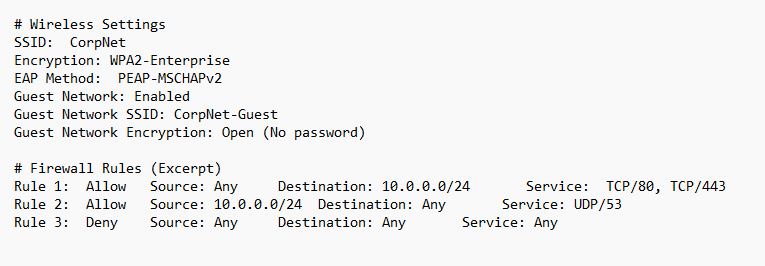
Vulnerability #1: Weak EAP Settings (Wireless)
- The Problem: Using the PEAP-MSCHAPv2 authentication protocol is risky. MSCHAPv2 has known vulnerabilities that allow attackers to crack captured network traffic and extract password hashes.
- Exploitation: With specialized tools, attackers within wireless range could intercept authentication traffic and potentially brute-force passwords, even on a WPA2-Enterprise network.
- Fix: Move to a stronger EAP method, like TLS-based authentication, that provides better protection against cracking attempts.
Vulnerability #2: Overly Broad Firewall Rules
- The Problem: Rules 1 and 2 create wide-open pathways for traffic. Allowing 'Any' source to access web services (Rule 1) or initiate DNS queries (Rule 2) is overly permissive, offering many potential entry points for attack.
- Exploitation: Hackers on the internet could probe for known vulnerabilities on services within the 10.0.0.0/24 network. Even minor flaws could offer footholds for lateral movement.
- Fix: Utilize the principle of least privilege. Restrict inbound firewall rules to only approved source networks or IP addresses. Consider stricter controls and monitoring on DNS to catch malicious domains.
Vulnerability #3: Open Guest Network
- The Problem: No encryption on the guest network means anyone nearby can sniff the traffic, potentially intercepting sensitive data transmitted by unsuspecting users.
- Exploitation: Attackers outside the building could join the guest network and launch attacks against network devices or other guests.
- Fix: Even guest networks deserve some security. Even basic WPA2-PSK encryption is significantly better than a completely open network.
Beyond the Flaws: The CISSP Bigger Picture Mindset
This challenge highlights the complex relationships in network security. Fixing one issue (stronger wireless authentication) requires awareness of firewall implications. Tightening the firewall could disrupt intended functionality if left unadjusted.
Here's where the CISSP shines: Understanding the big picture, prioritizing fixes based on risk, and ensuring network changes contribute to a holistically secure design.
Did any of these answers surprise you?
Were there other risks you picked up on?
While you are here: Did you enjoy CarlsCloud™ content today?
If so, buy me a coffee or just shoot me a note via LinkedIn to say thanks!